In the realm of secure communication, RSA encryption plays a pivotal role, offering a robust solution through its public-key cryptography. This blog post aims to demystify the intricacies of RSA encryption and decryption, using the versatile OpenSSL tool.
Overview of RSA #
RSA, named after its inventors Rivest, Shamir, and Adleman, relies on the mathematical properties of large prime numbers. It involves the generation of a public key for encryption and a corresponding private key for decryption. This asymmetry forms the basis for secure data transmission and digital signatures.
Setting Up OpenSSL #
Before delving into RSA operations, ensure you have OpenSSL installed. The installation process varies across operating systems, but OpenSSL’s command-line interface remains consistent.
# Install OpenSSL on Linux (Debian/Ubuntu)
sudo apt-get install openssl
# Install OpenSSL on macOS (using Homebrew)
brew install openssl
# Install OpenSSL on Windows
Download and install the binaries from https://slproweb.com/products/Win32OpenSSL.html
Generating RSA Key Pair #
Let’s kick things off by generating an RSA key pair. The following commands create a private key (private.pem)
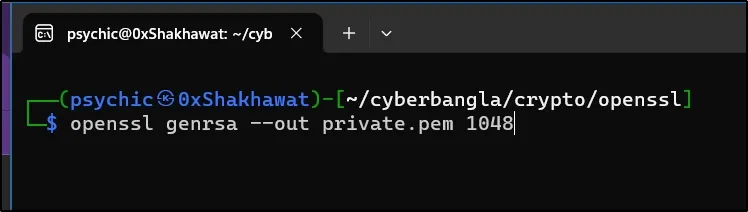
openssl genrsa --out private.pem 1024
I used 1048bit, you can use 2048bit or 3072bit for larger message encryption. I used (.pem) as an extension but you can use anything like (.txt), Etc. But (.pem) is better. PEM stands for Privacy Enhanced Mail.
Here is our private key:
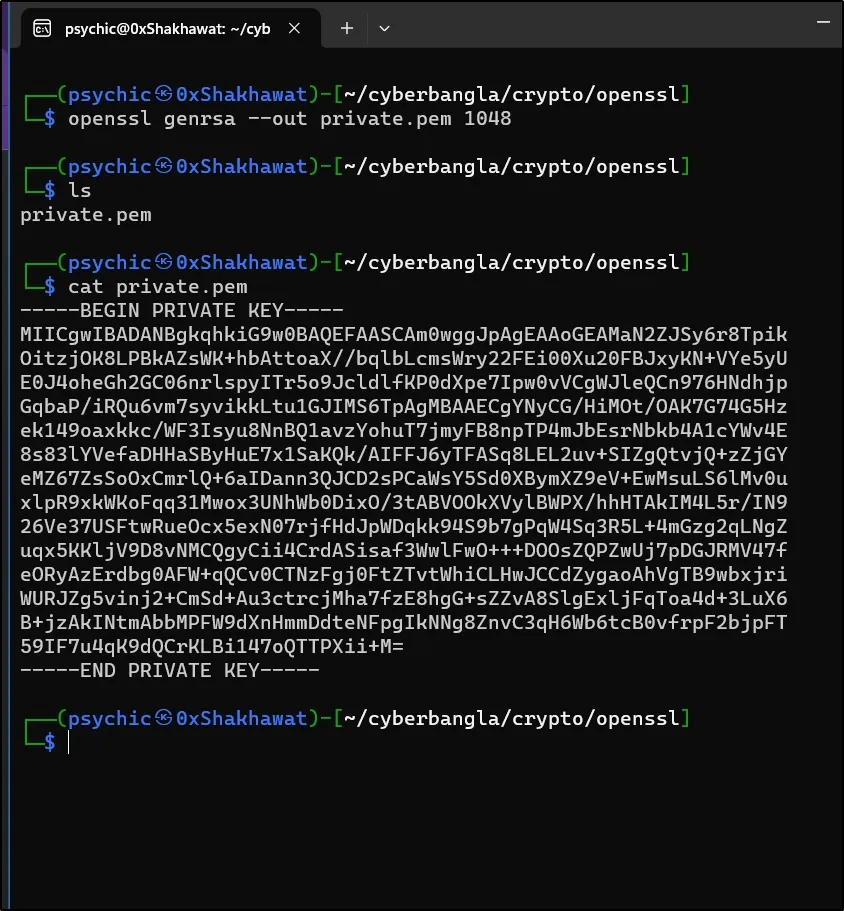
Let’s create a public key from this private key.
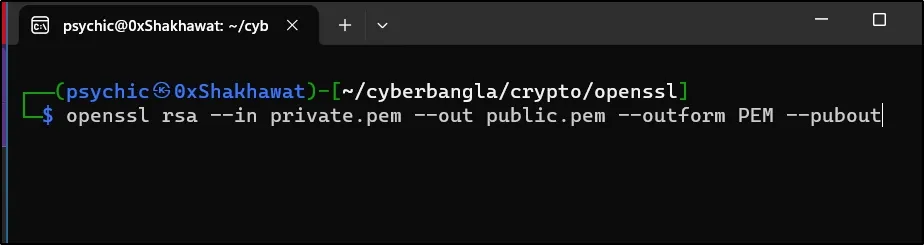
openssl rsa --in private.pem --out public.pem --outform PEM --pubout
I am using this command. Here is the result.
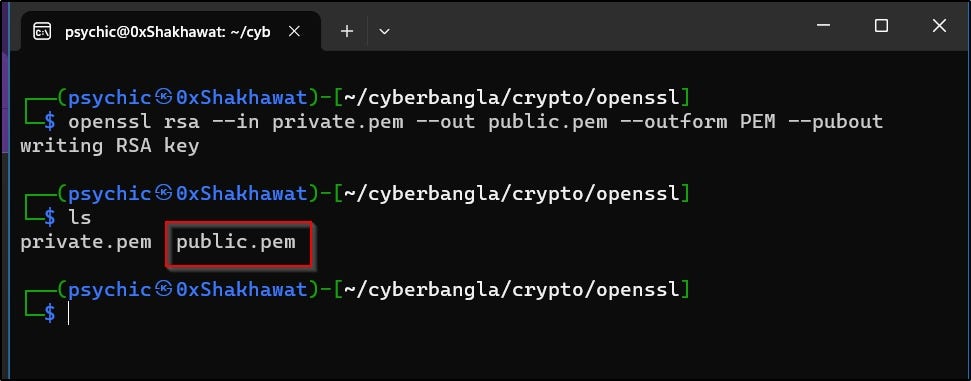

Creating a Message file I used echo to create a txt file message. The file name is “msg.txt”
echo "Hi friend. How are you?" >> msg.txt
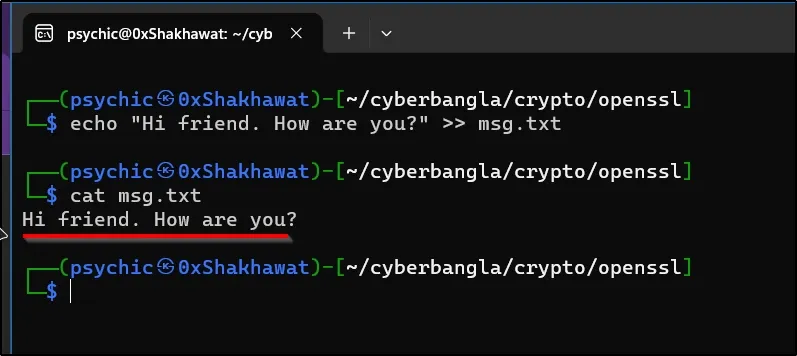
The message is: “Hi friend. How are you?”
Encrypting Data with RSA #
Now that we have our keys, let’s encrypt some data using the public key. This ensures that only the possessor of the private key can decrypt and access the original information.
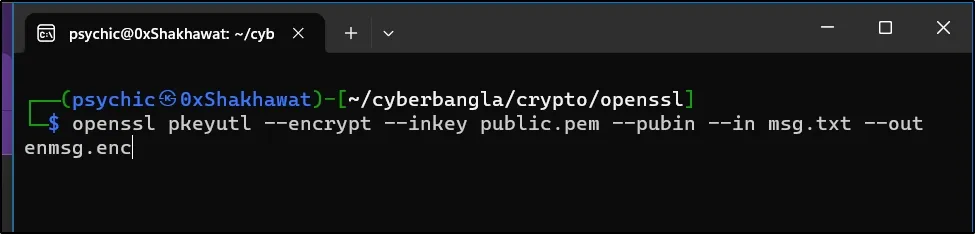
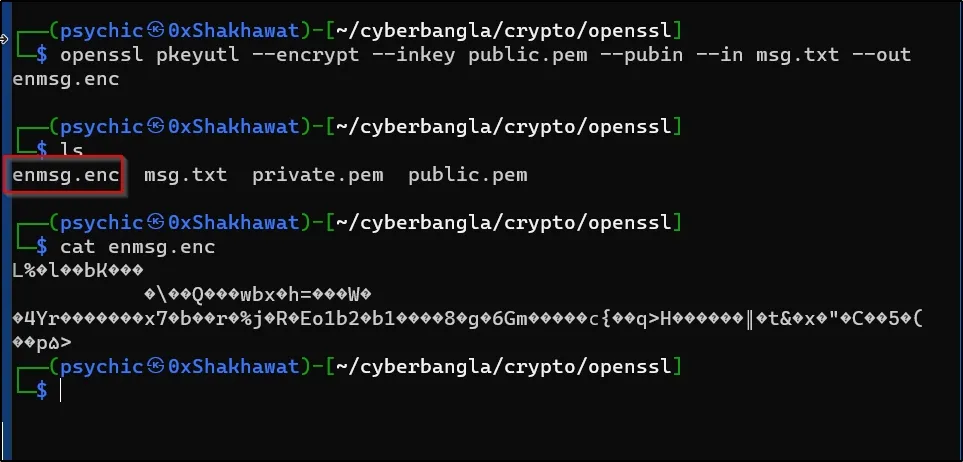
openssl pkeyutl --encrypt --inkey public.pem --pubin --in msg.txt --out enmsg.enc
now I have an encrypted data file named enmsg.enc
And I can safely delete my unencrypted message.
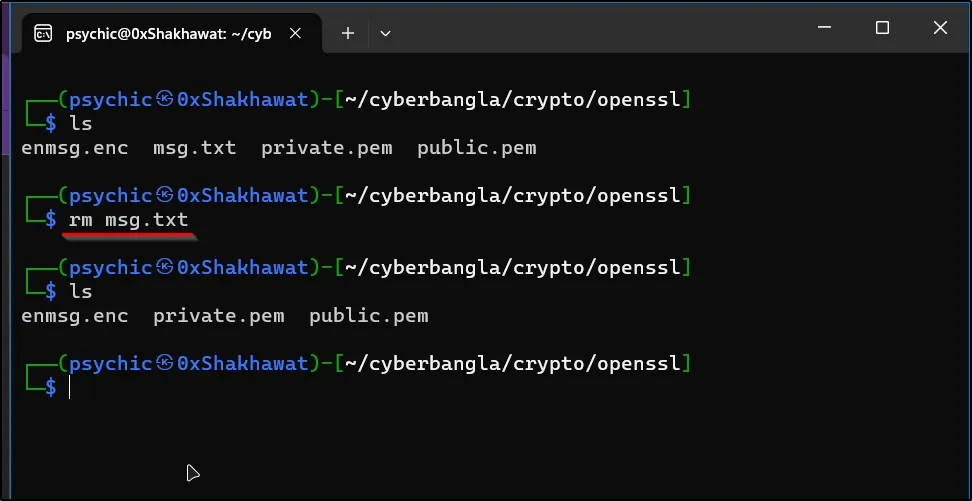
I use the rm command to remove the unencrypted message file.
now I have only an encrypted message file.
Decrypting Data with RSA #
To decrypt the data, we utilize the private key. This step ensures that only the rightful owner of the private key can reveal the original content.
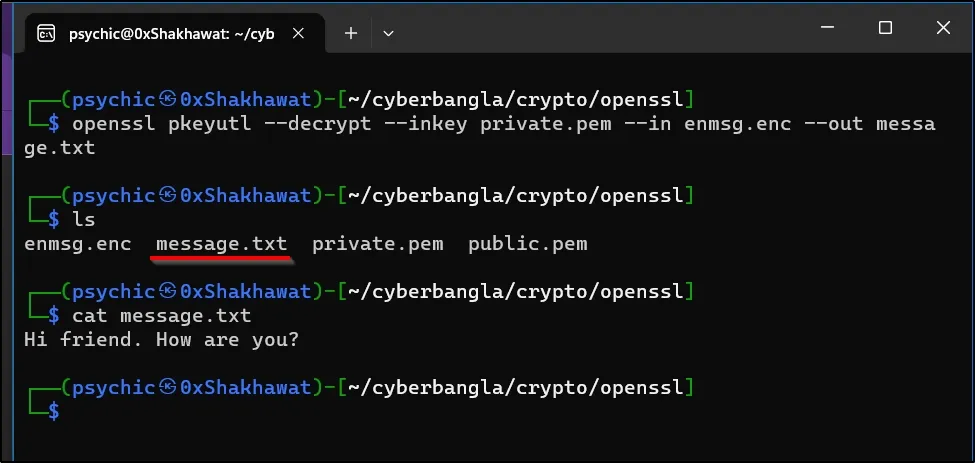
openssl pkeyutl --decrypt --inkey private.pem --in enmsg.enc --out message.txt
I used this command to decrypt the message. Now, I can view the message in plaintext.
Best Practices and Security Considerations #
As we venture into the cryptographic landscape, it’s essential to adopt best practices. Securely storing private keys and considering key length are crucial aspects. Regularly check for updates and be mindful of potential vulnerabilities associated with OpenSSL.
Conclusion #
In conclusion, RSA encryption and decryption, coupled with OpenSSL, provide a robust foundation for securing digital communication. By understanding the principles and practices outlined in this post, you’re equipped to navigate the intricacies of RSA cryptography.
Additional Resources #
For further exploration, refer to the official OpenSSL documentation, and consider practical exercises to deepen your understanding.
That’s it.
I also published blog this on my Medium Blog
You guys can subscribe to my YouTube channel 0xShakhawat My portfolio site: https://shakhawat.me
